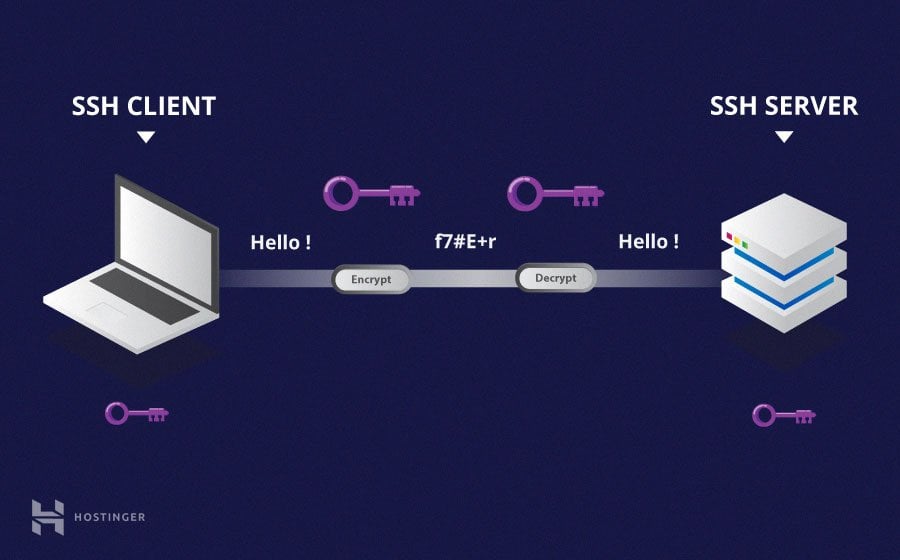
Comprehensive RemoteIoT Device SSH Tutorial: A Step-by-Step Guide
With the increasing adoption of IoT devices, understanding how to securely access and manage remoteIoT devices is essential. Whether you're a developer, system administrator, or hobbyist, mastering SSH (Secure Shell) for remoteIoT device management is a crucial skill. In this tutorial, we will explore everything you need to know about setting up and using SSH for remoteIoT devices.
IoT devices have transformed the way we interact with technology, enabling seamless connectivity and automation. However, managing these devices remotely can be challenging without the right tools. SSH provides a secure and reliable solution for accessing and controlling remoteIoT devices from anywhere in the world.
This tutorial is designed to equip you with the knowledge and practical steps to configure and use SSH effectively for remoteIoT device management. By the end of this guide, you'll have the confidence to set up SSH, troubleshoot common issues, and enhance the security of your IoT deployments.
Read also:Eminems Collaborations A Deep Dive Into His Iconic Partnerships
Table of Contents:
- What is RemoteIoT Device SSH?
- Setting Up SSH on a RemoteIoT Device
- Connecting to a RemoteIoT Device via SSH
- Enhancing SSH Security for RemoteIoT Devices
- Troubleshooting Common SSH Issues
- Automating SSH Tasks for RemoteIoT Devices
- Advanced SSH Features for RemoteIoT Devices
- Tools and Software for RemoteIoT SSH Management
- Best Practices for RemoteIoT Device SSH Management
- Conclusion
What is RemoteIoT Device SSH?
SSH, or Secure Shell, is a cryptographic network protocol that allows users to securely access and manage remote devices over an unsecured network. For RemoteIoT devices, SSH serves as a vital tool for maintaining connectivity and ensuring secure communication between the device and the user.
RemoteIoT devices often operate in environments where physical access is limited or impractical. SSH enables administrators to perform tasks such as file transfers, configuration updates, and real-time monitoring without being physically present at the device location.
Why Use SSH for RemoteIoT Devices?
- Secure communication through encryption.
- Reduced risk of unauthorized access.
- Compatibility with various operating systems and platforms.
- Support for automation and scripting.
Setting Up SSH on a RemoteIoT Device
Before you can use SSH to manage your RemoteIoT device, you need to ensure that the device is properly configured. Below are the steps to set up SSH on a typical RemoteIoT device:
Step 1: Enable SSH Service
Most RemoteIoT devices come with SSH pre-installed but disabled by default. To enable SSH:
- Access the device's configuration interface.
- Locate the SSH settings and enable the service.
- Restart the device to apply the changes.
Step 2: Configure SSH Settings
After enabling SSH, you can customize its settings to meet your specific requirements:
Read also:The Ultimate Guide To The Kardashian Names Exploring The Familys Legacy And Influence
- Set a strong password for the SSH user account.
- Consider using key-based authentication for added security.
- Specify the port number (default is 22) if needed.
Connecting to a RemoteIoT Device via SSH
Once SSH is set up on your RemoteIoT device, you can connect to it using a terminal or SSH client. Follow these steps to establish a connection:
Step 1: Gather Device Information
Before connecting, ensure you have the following details:
- Device IP address.
- Username and password (or SSH key).
- Port number (if different from the default).
Step 2: Use an SSH Client
On a Linux or macOS system, you can use the built-in terminal to connect:
Command: ssh username@device_ip
For Windows users, tools like PuTTY or Windows Terminal can be used for SSH connections.
Enhancing SSH Security for RemoteIoT Devices
Security is paramount when managing RemoteIoT devices via SSH. Below are some best practices to enhance SSH security:
Use Key-Based Authentication
Instead of relying on passwords, consider using SSH keys for authentication:
- Generate a public-private key pair.
- Copy the public key to the RemoteIoT device.
- Disable password-based authentication in the SSH configuration file.
Change Default SSH Port
Changing the default SSH port (22) can help reduce the risk of automated attacks:
- Edit the SSH configuration file (
/etc/ssh/sshd_config). - Set a custom port number.
- Restart the SSH service to apply the changes.
Troubleshooting Common SSH Issues
Even with proper setup, SSH connections can sometimes fail. Here are some common issues and their solutions:
Connection Timeout
Cause: Network issues or incorrect IP address.
Solution: Verify the device's IP address and ensure network connectivity.
Authentication Failure
Cause: Incorrect username, password, or key.
Solution: Double-check the credentials and ensure the correct key is being used.
Automating SSH Tasks for RemoteIoT Devices
SSH can be used to automate repetitive tasks, saving time and effort. Below are some examples:
Script-Based Automation
Create a bash script to automate SSH commands:
Example:
#!/bin/bash
ssh username@device_ip "sudo systemctl restart service_name"
Scheduled Tasks
Use tools like cron to schedule SSH tasks:
- Edit the crontab file:
crontab -e. - Add a new entry for the desired task.
Advanced SSH Features for RemoteIoT Devices
SSH offers several advanced features that can enhance your RemoteIoT device management experience:
Tunneling and Port Forwarding
SSH tunneling allows you to securely access services running on a RemoteIoT device:
- Set up a local tunnel:
ssh -L local_port:destination_host:destination_port username@device_ip. - Set up a remote tunnel:
ssh -R remote_port:local_host:local_port username@device_ip.
SSH Multiplexing
Multiplexing allows you to reuse existing SSH connections, reducing latency and resource consumption:
- Add the following lines to your SSH configuration file:
ControlMaster autoControlPath ~/.ssh/controlmasters/%r@%h:%p
Tools and Software for RemoteIoT SSH Management
Several tools and software can simplify SSH management for RemoteIoT devices:
SSH Clients
- Putty (Windows).
- Terminal (macOS/Linux).
- Windows Terminal (Windows 10/11).
SSH Management Platforms
- JumpCloud.
- SSH.com.
- KeyCDN's SSH Gateway.
Best Practices for RemoteIoT Device SSH Management
Adopting best practices ensures efficient and secure management of your RemoteIoT devices:
Regularly Update SSH Software
Keep your SSH software up to date to protect against vulnerabilities:
- Check for updates regularly.
- Apply patches promptly.
Monitor SSH Logs
Regularly review SSH logs to detect and respond to suspicious activity:
- Use tools like Logwatch or Splunk for log analysis.
- Set up alerts for unusual login attempts.
Conclusion
In this comprehensive RemoteIoT Device SSH Tutorial, we've explored the essential aspects of using SSH for managing IoT devices. From setup and connection to advanced features and security enhancements, mastering SSH empowers you to efficiently and securely control your RemoteIoT devices.
We encourage you to apply the knowledge gained from this tutorial in your IoT projects. If you found this guide helpful, please share it with others and explore more resources on our website. Your feedback and questions are always welcome in the comments section below!
References:
Article Recommendations